Improved Dependency Submission for GitHub Actions
Recently someone brought to my attention that when pin your actions, Security Advisories for GitHub actions do not show up in the Dependency Graph. I set about a solution to solve that problem.

If you've read some of my earlier blogs about GitHub Actions Security, you may have followed my advice to pin your actions and configure Dependabot. Recently someone brought to my attention Security Advisories for GitHub actions do not show up in the Dependency Graph in that case and Dependabot won't create security updates.
I decided to solve that problem.
Background
When a security vulnerability is found and a security advisory is created, it will have the action and its affected versions as metadata. Versions, not SHAs.
When Automatic Dependency Submission submits the versions of actions used by a repository it records:
@v1.2.3as1.2.3@v1as1.*.*8e8c483db84b4bee98b60c0593521ed34d9990e8as8e8c483db84b4bee98b60c0593521ed34d9990e8
The Security Advisory Database can't match 8e8c483db84b4bee98b60c0593521ed34d9990e8 against the vulnerable version range and won't show the vulnerability in the dependency graph.
Another issue exists when actions are forked to an organization (a common technique to create a private actions marketplace). The dependency is recorded using the organization name that holds the fork, not the upstream.
The Security Advisory Database can't match myorg/actions_checkout against the vulnerable action actions/checkout and won't show the vulnerably in the dependency graph.
Impacted features
Without recording the exact version of each action used, a number of features won't work as you might expect:
- Dependency Graph won't show which actions you use are vulnerable.
- Dependabot Security Updates won't be created for workflows using vulnerable actions.
- Dependency Review Action won't block pull requests introducing vulnerable actions into your workflows.
Solution
To solve the issue I created a new manual submission action which mimics the automatic submission, but adds a few extra features:
- It resolves the SHA to the highest, most specific version and records that as an additional dependency.
- It resolves a wildcard version to the current specific version and records that as an additional dependency.
- It can be configured to look up the upstream of a forked action and records that as an additional dependency.
With these additional dependencies recorded, the Dependency Graph now contains all the metadata to determine whether the GitHub actions you depend on are vulnerable and all features should now work as expected.
How to
Changing how Actions' dependencies are reported, you simply add my jessehouwing/actions-dependency-submission action to your workflows (and optionally add actions/dependency-review-action:
name: Submit and validate dependencies of GitHub Actions
on:
push:
branches:
- main
pull_request:
schedule:
- cron: '33 4 * * *'
permissions: {}
jobs:
submit-actions-dependencies:
runs-on: ubuntu-latest
permissions:
# submitting dependencies requires 'contents: write'
contents: write
steps:
- uses: actions/checkout@8e8c483db84b4bee98b60c0593521ed34d9990e8 # v6.0.1
- uses: jessehouwing/actions-dependency-submission@62d04cd44fb55157bdf0aff579284bf2304f3ef0 # 1.0.5
with:
token: ${{ secrets.GITHUB_TOKEN }}
- uses: actions/dependency-review-action@3c4e3dcb1aa7874d2c16be7d79418e9b7efd6261 # 4.8.2
if: github.event_name == 'pull_request'
with:
retry-on-snapshot-warnings: trueYou can test whether the action is working correctly by adding a vulnerable action to your repository:
name: Vulnerable Dependencies
on:
workflow_dispatch:
jobs:
vulnernable-dependencies:
if: false
runs-on: ubuntu-latest
permissions: {}
steps:
- uses: actions/download-artifact@eaceaf801fd36c7dee90939fad912460b18a1ffe # v4.1.2This should show as a high vulnerability in the Dependency graph of the repository:
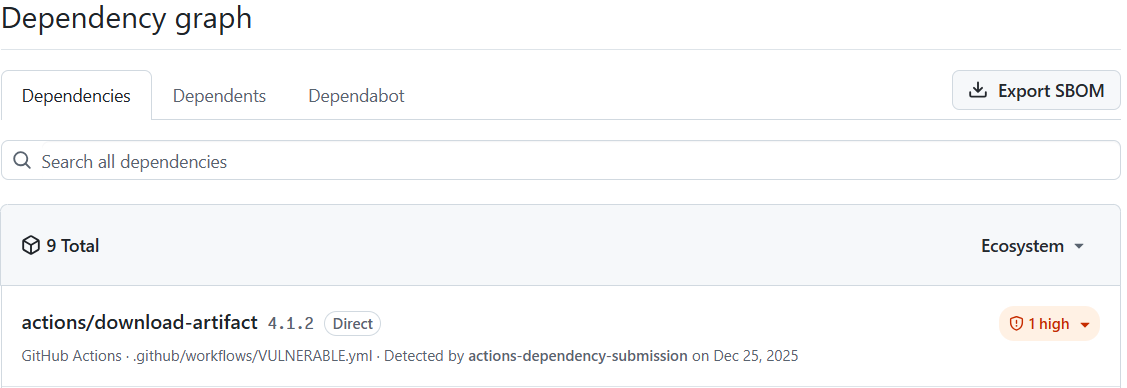
actions/download-artifact@v4.1.2 as vulnerable.And you'll also see the original report using the SHA:
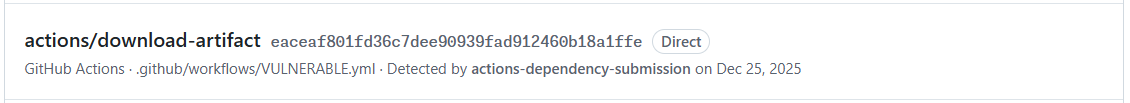
actions/download-artifact referenced by SHA.You can find the action and additional documentation and examples here: