Enable RenovateBot for Azure Pipelines
In my report on the Security state of the Azure DevOps Marketplace I came to the unfortunate conclusion that about 40% of the extensions contain vulnerabilities. One of the recommendations for both Azure DevOps administrators and pipeline authors was to keep the Azure Pipelines Tasks up-to-date.

Unfortunately it's hard to do that. The old UI based pipelines only show a minimal indicator and in YAML there is no indication at all. Until today. That is, if you are a RenovateBot user, use YAML pipelines and have enabled the new Azure Pipelines Preview feature:
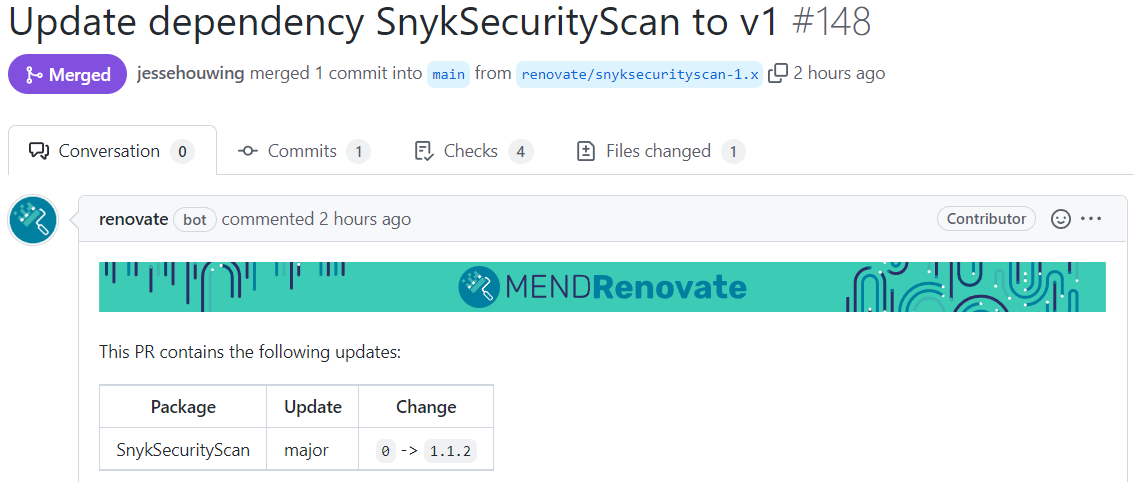
As of version 34.92.0, Renovate now automatically suggests updates for tasks installed through the Azure DevOps Marketplace for all public extensions. And the suggestions are updated weekly on Sunday.
Installation
GitHub
If your sources are stored in GitHub, you can install the Renovate app from the GitHub marketplace and grant it access to your repositories. Once you've done that you can configure Renovate through the renovate.json file in your repository, or by putting a central configuration in your .github repository.
For now you must explicitly activate the Azure Pipelines support:
{
"$schema": "https://docs.renovatebot.com/renovate-schema.json",
"extends": [
"config:base"
],
// To enable Azure Pipelines support add:
"azure-pipelines": {
"enabled": true
},
// If you only want to get pull requests for updates from @1 to @2
// instead of @1.1.2 to @1.1.5 add:
"packageRules": [
{
// Only extract major versions for Pipeline Tasks
"matchDatasources": ["azure-pipelines-tasks"],
"extractVersion": "^(?<version>\\d+)"
}
]
}.github/renovate.jsonAzure Repos
As with GitHub, you must enable the Azure Pipelines support in the config file. You must store it in the root of each repository that contains the pipelines you want to service:
{
"$schema": "https://docs.renovatebot.com/renovate-schema.json",
"extends": [
"config:base"
],
"azure-pipelines": {
"enabled": true
}
}/renovate.json
If your sources are stored in Azure Repos you have two options:
RenovateMe Extension
You can use the RenovateMe extension from an Azure Pipeline to run Renovate against your repositories. The steps to enable RenovateMe are explained in the extension's documentation.
Calling renovate yourself
Or you can call Renovate from an Azure Pipeline explicitly:
- bash: |
git config --global user.email 'bot@renovateapp.com'
git config --global user.name 'Renovate Bot'
npx --userconfig .npmrc renovate
env:
TOKEN: $(System.AccessToken)All the steps to setup the pipeline are explained here.
How does it work?
The support for Azure Pipelines consists of 2 parts. One takes care of the built-in tasks, the other of the tasks from the Azure DevOps marketplace.
The built-in tasks were already supported by Renovate. There is a job that runs weekly that scans the microsoft/azure-pipelines-tasks repository and adds all the versions it finds there to a static datafile.
I've added a new job that indexes the Azure DevOps Marketplace by downloading every public vsix ever published and extracting the relevant version information. The result of this job is another static datafile that is added to renovate on a weekly basis.
What next?
Next I'll be looking to add a datasource for Azure Pipelines that retrieves the available versions straight from your Azure DevOps organization. That would enable updates of private extensions as well as tasks that were installed directly into the organization using tfx build tasks upload.
If you want to support me, please consider:


